As an M365 Administrator, there will most likely come a time when you’ll want to block a specific user’s access to SharePoint Online. I ran into this issue recently for a client of mine, and I found the resources online lacking, so why not share what I’ve learned?
Before we begin, please note that blocking SharePoint Online access will block access to OneDrive as well. We accomplished blocking SharePoint Online using a Conditional Access policy. To utilize Conditional Access policies, your organization needs to have one of the following licenses:
- Azure Active Directory Premium P1 or P2,
- Microsoft 365 Business Premium,
- Microsoft 365 E3 or E5, or
- Enterprise Mobility and Security E3 or E5.
You may already be using Conditional Access policies for a variety of reasons. Some include enforcing MFA while excluding trusted location, or maybe you only allow logins to your tenant from within certain countries. Conditional Access policies offer a wide variety of options. For more information on Conditional Access policies in Azure see: Building a Conditional Access policy – Azure Active Directory – Microsoft Entra | Microsoft Learn.
The first step in building our Conditional Access policy is to log into the Azure Active Directory Admin Center. Then under “Security” there is a “Conditional Access” tab.
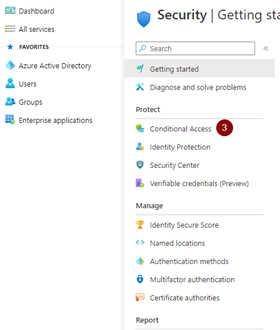
Then under “Conditional Access,” we can select the “Policies” tab and then “New policy.”
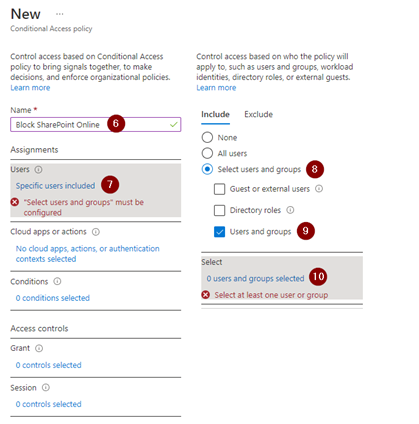
Next, we name our policy, “Block SharePoint Online,” then select the users or groups we want to block. In my situation I targeted one specific user, but in other situations you may want to create a security group and target that instead.
Next, you’ll click “Cloud app or actions” and include “Office 365 SharePoint Online.”
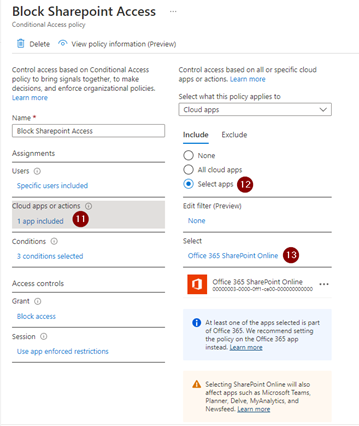
Next, you’ll set your conditions. Here I’m targeting “Any Device” for “Device Platforms,” “Any location” for “Locations,” and all “Client Apps.”
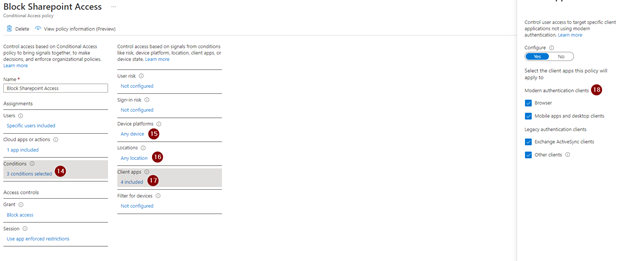
Next set “Grant” to “Block Access.”
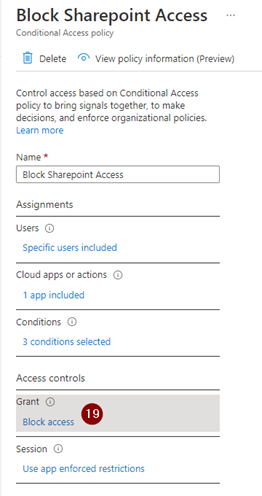
Next, set “Session” to “Use app enforced restrictions.” This is key, and the policy will not work if this is not set.

Once you are ready, change the policy from “Report-only” to “On.”
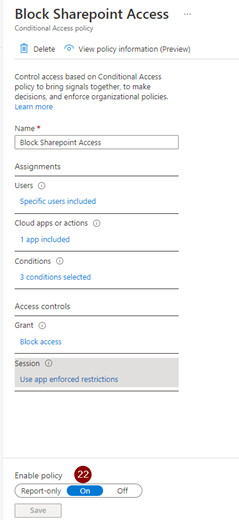
With this policy enabled, users will not be able to access SharePoint or OneDrive from any device.
In my situation, my client required a third party user to have an email address within their tenant, but of course they did not want this third party to have access to all the company data within SharePoint. This Conditional Access policy allows the third party to continue using email while protecting the company data.
If you have questions or need assistance, please reach out to us!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









