The old saying, “the pen is mightier than the sword,” might need a modern-day update, as it seems that the keyboard has become mightier than the pen, with our online activities significantly impacting our daily lives. While we can connect with people all over the world and access a wealth of information online, we also expose ourselves to the growing threat of malicious websites capable of compromising our devices and personal information. To protect ourselves on the internet, it’s important to follow some essential tips on how to detect and avoid malicious websites.
What is a Malicious Website?
A malicious website is a site that an attacker has designed to trick users into (a) downloading malicious software, (b) submitting credentials or other sensitive information, or (c) making payments to a scammer. According to the 2022 Google Transparency Report, Google detected over 3 million potentially harmful websites!
When Do Users Come Across These Sites?
Users typically come across malicious websites after clicking on links in an email (i.e., as part of a phishing attack). However, users might also click links in text messages they receive or ads that they see.
What Can Users Do to Protect Themselves?
There are a number of ways users can detect malicious websites and protect themselves from falling victim.
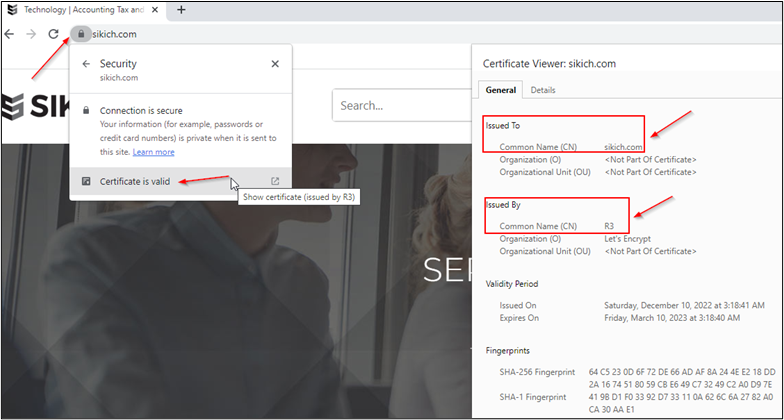
Look for the Lock Icon
Users can look for the lock icon that suggests a connection is secure, which is usually found to the left or far right of the URL. By clicking on the icon, a prompt will appear where the user can view the certificate for the page. Users can look to see if the SSL certificate was issued to a Common Name (CN) that they would expect to be associated with the website, and if that certificate was issued by a reputable third-party Certificate Authority (CA).
Most sites use Hypertext Transfer Protocol Secure (HTTPS) rather than the Hypertext Transfer Protocol (HTTP). Seeing “https” in the URL indicates that the site is protected by an SSL certificate. This is important as HTTPS encrypts communication between the server and the user, while HTTP transmits all information, including sensitive data like usernames and passwords, in clear text. HTTPS helps prevent man-in-the-middle attacks and the stealing of clear-text credentials from the network. However, it’s important to note that some sites have not yet made the upgrade to HTTPS, and not all URLs using HTTPS are safe, as anyone can create certificates to make URLs use HTTPS and appear to be secure.
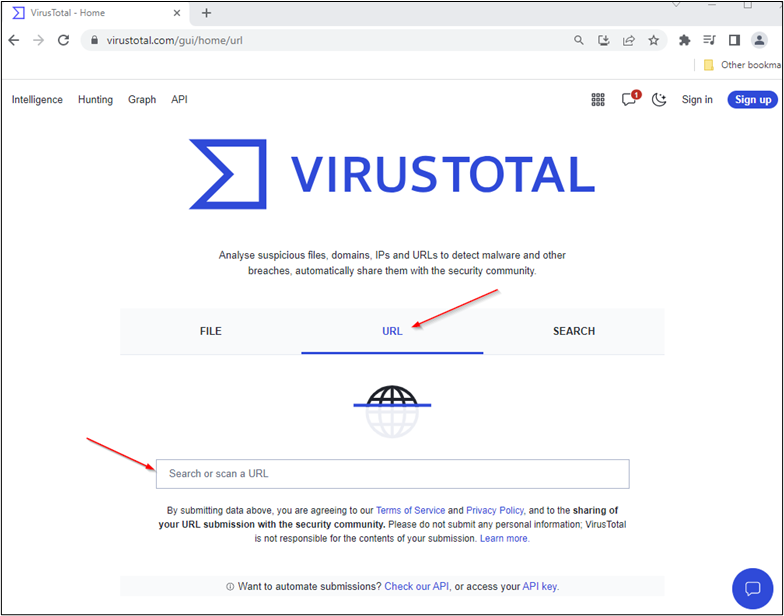
Use Website Scanners
Users can use online tools, such as the one available at https://virustotal.com, to scan websites for indicators that a website may be malicious.
Be Wary of Malware and AdWare
Malicious sites may present prompts to download software that an attacker can use for malicious purposes (i.e., malware). For example, a pop-up might claim that your computer needs updates. A malicious website may do this by indicating that a device is infected with malware or that a browser’s extensions or software is out of date.
Other malicious sites may claim that you have won a prize and request your personal information to claim it. This is known as adware.
Pay Close Attention to Details
Users should be on the lookout for suspicious URLs. For example, https://sikich.com is our company website. However, attackers may try to trick users into visiting a malicious website by placing it at a URL that has a similar spelling to a known safe website, for example, https://sikiich.com. Alternatively, an attacker could try to associate the malicious website with a legitimate site by leveraging subdomains to try to add legitimacy. For example, an attacker could host a malicious website at https://sikich.[malicious_site.com].
It’s also possible that a link to a malicious website could appear as an IP address instead of a URL (e.g., https://142.250.191.142). Of course, it’s important to keep in mind that not all IP addresses are malicious and not all URLs are safe.
Given the prevalence of malicious websites, users need to remember to stay vigilant and think twice before clicking on links or entering personal information into a website.
If your company could benefit from security awareness training or social engineering testing related to phishing attacks, please reach out to our team and we’ll be happy to help.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









