Cybersecurity and risk management are paramount for every business, but it’s especially so for businesses working with the Department of Defense (DoD). The Cybersecurity Maturity Model Certification (CMMC) is a critical framework designed to protect sensitive information. This article will guide SMBs through the essential steps to achieve CMMC compliance and manage associated risks effectively.
1. Understanding CMMC Levels
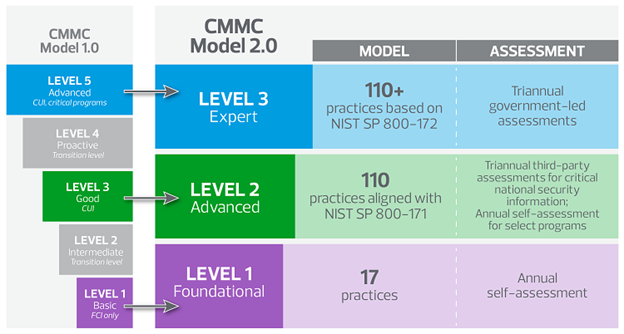
The CMMC framework now consists of three levels, each representing a different degree of cybersecurity maturity.
CMMC Levels:
- Level 1: Foundational – Focuses on basic safeguarding of Federal Contract Information (FCI) with 17 practices and an Annual self-assessment.
- Level 2: Advanced – Serves as a transitional step towards more advanced practices, with 110 practices aligned with NIST SP 800-171. Triannual third-party assessments are required for critical national security information; Annual self-assessment is required for select programs
- Level 3: Expert – Implements the most advanced practices to protect CUI from APTs, requiring 110+ practices based on NIST SP 800-172 and triannual government-led assessments.
Each level is designed to ensure that contractors can adequately protect sensitive information based on the type of contracts they handle.
A summary of the consolidation of levels is below.
2. Initial Assessment
Before diving into the implementation, it’s crucial to conduct an initial assessment.
Gap Analysis:
- Identify the current state of your cybersecurity practices.
- Compare them against the requirements of the desired CMMC level.
Identifying Areas Needing Improvement:
- Highlight specific areas where your current practices fall short.
- Develop a plan to address these gaps.
3. Implementation of Controls
Once the gaps are identified, the next step is to implement the necessary controls.
Key Security Controls Required for Compliance:
- Access Control: Ensure only authorized personnel have access to sensitive information.
- Incident Response: Develop and implement an incident response plan.
- Risk Management: Continuously assess and manage risks.
Practical Tips for Implementing These Controls:
- Use multi-factor authentication (MFA) to enhance access control.
- Regularly update and patch systems to mitigate vulnerabilities.
- Train employees on cybersecurity best practices.
4. Continuous Monitoring
Achieving compliance is not a one-time effort; it requires ongoing vigilance.
Importance of Ongoing Monitoring and Assessment:
- Regularly review and update security measures to address new threats.
- Conduct periodic audits to ensure continued compliance.
Tools and Techniques for Effective Monitoring:
- Use automated tools for real-time monitoring and alerts.
- Implement a Security Information and Event Management (SIEM) system to analyze security data.
5. Preparing for Certification
The final step is to prepare for the CMMC audit.
Steps to Prepare for a CMMC Audit:
- Compile documentation of all implemented controls and practices.
- Conduct a pre-assessment to identify any remaining gaps.
- Address any issues found during the pre-assessment.
Choosing the Right CMMC Third-Party Assessment Organization (C3PAO):
- Select a C3PAO with a proven track record and relevant experience.
- Ensure they understand the specific needs and challenges of your business.
Achieving CMMC compliance and managing risks are crucial for SMBs to secure DoD contracts. By following these steps, businesses can meet requirements, protect sensitive information, and unlock new growth opportunities with the DoD.
Free Assessment Offer
Stay compliant and ensure operational success with our free Microsoft 365 Security Assessment. You can safely access the assessment form here. The assessment analyzes threat detection, data protection, compliance, and incident response.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









