Office 365 services operate off a token expiration and refresh mechanism. This is a standard method used for authentication across the IT industry. This mechanism works in Office 365 by issuing a token, which is valid for one hour, to a client when it authenticates against a service. When the token expires the client reaches back out to the identifying service, Azure AD, and refreshes the token. At this time a reevaluation is done to verify user access is still allowed.
This method, while good for providing an optimal end user experience, has a major pitfall regarding its lag time between when the token is issued and when it refreshes, and what changes may have occurred since. These changes could include things like password expiration, account deactivation, network location change, and so on. A real-life example would be that a person is terminated, and their account immediately disabled, however, because their mobile mail client just got a fresh token, they still have access to send and receive e-mail for the next 45 minutes. You could see where IT security professionals and management alike would have a concern with this.
Aware of this gap, Microsoft has introduced a new mechanism called continuous access evaluation (CAE). Continuous access evaluation allows for near real-time evaluation of events and enforcement of changes. This allows for immediate revocation of account access if someone loses a device or discovers their account has been compromised.
Besides acting against an account based on a critical event, CAE also allows for Conditional Access policies to be enforced more immediately. For example, if you have a policy that only allows for access to your SharePoint Online environment from devices when they are on the corporate network, and a person takes their PC to the café across the street and connects to their public Wi-Fi, they will be locked out of SPO immediately instead of potentially maintaining access for up to an hour.
To allow for CAE, clients must be using a new mechanism called claim challenge. Previously, a client would try to refresh the access token from its cache as long as it was not expired. With claim challenge, the client can be informed to bypass a cached token even if it has not yet expired. This new mechanism is available in the latest versions of Outlook, Teams, and Office on all major platforms (Windows/Mac/iOS/Android).
CAE is in public preview at the time of this writing. It currently supports enforcing access revocation based on the below critical events for Exchange Online and SharePoint online:
- User Account is deleted or disabled.
- Password for a user is changed or reset.
- Multi-factor authentication is enabled for the user.
- Administrator explicitly revokes all refresh tokens for a user.
- Elevated user risk detected by Azure AD Identity Protection.
Since it is in preview, it must be manually enabled from your Azure portal:
- Browse to Azure Active Directory> Security > Continuous access evaluation.
- Choose Enable preview.
You can also manually initiate a sign out of all user sessions, a good idea to do for any termination, or report of a lost device or compromised account, from the Office 365 Admin Center as shown in the below screenshot.
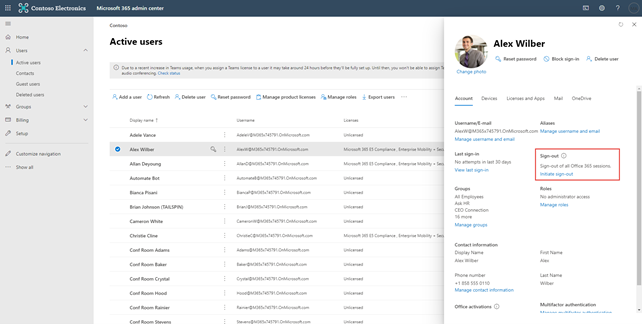
I anticipate that Microsoft will look to enable CAE on all tenants down the road, once it is no longer in the preview state.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









