In a previous blog post, we discussed what a radio frequency identification (RFID) access card is, what the risks associated with RFID cards, how to protect yourself when using access cards and why being careful when using RFID cards is important. In this blog post, we’ll discuss the types of attacks that can be performed against an RFID-based access control system, as well as a few ways to protect against such attacks.
RFID cards are very simple devices, which makes them reliable for everyday use. However, it also makes them an easy target for attackers looking to gain access to a facility. In this post, we’re focusing on low-power RFID cards, which are commonly used in door access systems. There are a wide variety of attacks that can be performed against RFID access systems. The majority of attacks against RFID systems can be broken into three major categories: man-in-the-middle (MITM), cloning, and brute forcing.
Man-in-the-Middle
An attack you may have heard about in the networking world is the MITM attack. An MITM attack is when an attacker is able to intercept and copy sensitive information between a victim and the victim’s intended recipient of the information. An MITM attack against an RFID system uses a hardware device to capture and decode the RFID signal between the victim’s card and a card reader. The malicious device then decodes the information and transmits it to the attacker so they can replay the code and gain access to the building. Many times, this hardware device is battery powered and simply placed on top of the legitimate card reader. When a user passes their RFID card over the reader, the attacker’s device copies the signals for later use by an attacker and allows the signals to go to the reader so that a user does not become suspicious by a door suddenly seeming inaccessible.
Another example of an MITM attack involves placing a small hardware device in line with a card reader and the controller, which is responsible for validating the credentials being read by the card reader. A controller connects to the access control server and stores a copy of valid cards in its internal storage. The controller is generally located near the doors for which it is responsible, such as above a drop ceiling. As seen in Figure 1 – ESPKey, these devices have five wire taps that connect into the wires running between the reader and the controller. The ESPKey is a mass-produced hardware device built to capture the communications across the wire and store it for later use by the attacker. These pieces of hardware are so small that, after the RFID cover is removed, they fit inside the RFID card reader housing, which obscures them from view.
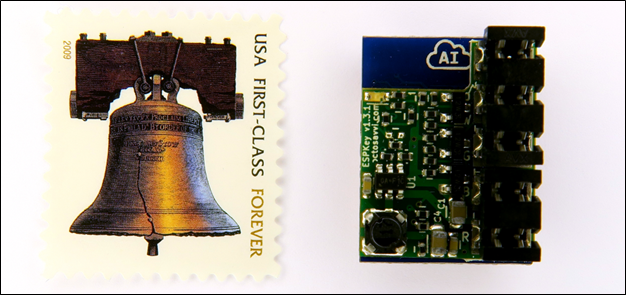
Many organizations struggle with how to prevent MITM attacks, since most end users would not typically notice if a card reader is suddenly a different shape or size due to an attacker having placed their own device inline, or identify that a cover has been removed and the wires have been trapped into. Depending on the type of RFID access control system your company uses, the system may support anti-tamper features such as using additional wires to create an electrical circuit. When the RFID reader is removed or opened, the circuit is broken. This alerts the controller that the system may have been tampered with and to shutdown the reader or take other actions. Look to make sure all the anti-tamper features of your system are in place and working. The anti-tamper controls should be tested on a regular basis along with other physical security controls.
Another option to assist in detecting tampering is to have security cameras that focus on each door, with the RFID reader in view. Almost all security camera systems now offer motion-sensing reporting. This allows for a large amount of uneventful time to be skipped on the recording, allowing a user to quickly view any possible tampering or suspicious activity.
One solution is to implement anti-tamper screws to secure the RFID reader housing. While anti-tamper screw drivers are available such that an attacker could acquire one, the screws still serve to increase the barrier to entry.
Cloning
Another common technique attackers use to defeat RFID access systems is to clone (i.e. copy) a user’s RFID card without their knowledge. An attacker does not always need physical access to the RFID card to clone it. In fact, an attacker can capture the information stored on an RFID card from several feet away using off-the-shelf components and write the data to a blank compatible RFID card. Many times, these cloning devices are built using components from a large RFID reader that is used for parking garages or other areas where a user cannot get close to the card reader to scan their card.
These low-cost cloning devices can be used by an attacker as they walk past a member of your staff on the street or in a coffee shop. Once an attacker has copied the information from the victim’s RFID card, they can clone it on to a blank RFID card for use at your facility.
When employees are in the office, it is generally preferred that they wear their RFID card out in the open, as it sometimes displays their identification. Protecting against long-range cloning attack can be difficult, but there are a few options to mitigate this type of attack in the office:
- Separate identification details, such as photo IDs, from RFID cards. This way, an employee can wear their identification around the office and protect their RFID card inside an RFID-blocking sleeve or wallet.
- If the identification details cannot be separated from the RFID card, have employees wear their credentials above their waist, such as clipped to their lapel. This makes it more likely that an employee would notice someone who is trying to clone the employee’s card.
If an attacker gets close to one of your employees in a public space or while they are at lunch, protecting their RFID card is significantly harder than it would be in the office, as your employees are less likely to be looking for anything out of the ordinary. The best solution for this scenario is for employees to leave their card secured off their person (e.g. in their vehicle), away from the eyes and reach of potential attackers. If an employee does not have the ability to leave their badge in a secure location, an RFID blocking sleeve should be used.
Brute Forcing
Another attack you may have heard of is a brute-force attack. When attacking something like a login portal, a brute-force attack would involve the attacker submitting randomly generated credentials to the login in the hopes of finding a match to gain access to the application. This same type of attack can be used against an RFID system. An attacker can use a hardware device to submit random combinations of RFID identifiers to the access control system in the hopes that one identifier will grant them access. This attack is not often used, as it is very time consuming and generally unsuccessful without a base level of information. RFID cards many times contain a facility code or other specific identifiers that cannot be quickly guessed. If an attacker captures that data from a known-valid card, the final identifier of another employee’s RFID credentials can be brute forced with significantly fewer guesses. This could allow an attacker to leverage information obtained from one employee’s card to brute force a higher level of access.
By adequately protecting RFID cards and readers using the best practices previously described can keep an attacker from capturing data from a valid card. If an attacker cannot obtain the facility code or other identifiers, brute forcing will be too time consuming to for the attack vector to be viable.
Alternatives to RFID
There are options that offer more security than RFID systems, such as contactless smart cards or readers that leverage Bluetooth so a user’s access card can be stored in their mobile device. Contactless smart cards contain a small microprocessor that uses an asymmetric cryptographic function to send the credentials to the card reader. This is more secure than RFID, which simply broadcasts the credentials when power is present. Contactless smart cards can also be used to authenticate users into workstations or other systems. Using a mobile device for access control allows for a secure vendor-provided mobile app to manage tokens. It also lowers the risk of user’s losing, misplacing or leaving their access card at home, since most users have their mobile device with them at all times. As with most items in security, the question ultimately comes down to the level of resources an organization is willing to commit to security versus how much risk they are willing to accept.
Wrap Up
We touched on just a few simple attacks that malicious actors can take against an organization’s RFID access control systems. Most of these attacks involve little cost or effort and can be very effective. It is a good idea to examine the risk profile of your organization and assess how many controls should be implemented around your RFID system. Training employees can go a long way toward helping secure your environment.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









