This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
The Importance of Internal Network Penetration Testing

Focusing on locking your network down from the outside is great. However, the hard truth is that, in all likelihood, someone will get in sooner or later. If and when an attacker does get in, what do you have in place to stop them? You might assume that your internal firewall will keep things segregated. But have you ever tested its configurations? Have you ever examined how an intruder on your network might be able to move from one environment to another if they ever found their way in? While performing external vulnerability scans (which should not be confused with external penetration testing) and having a firewall in place are important pieces in a layered security approach, it is imperative that your network also be manually tested from the inside to better prepare your organization for a situation in which your perimeter defenses fail.
It Will Never Happen to Us
You may think that your network is secure and that attackers cannot get in. However, the Sikich Cybersecurity practice manages to identify vulnerabilities in the networks of some of its most security-conscious clients. On a recent test of a long-time client, Sikich identified that a user who had accounts in both the client’s “secure” and “non-secure” environments used the same password for both of their accounts. Sikich was eventually able to capture and crack the user’s password hash from the “non-secure” environment to obtain the clear-text password. Once Sikich found that the user reused their password in the “secure” environment, Sikich wrote malicious code to bypass the anti-virus and anti-malware in place and leveraged the compromised account to obtain access to several different hosts within the client’s “secure” environment.
Even for organizations that take security seriously, it is important to perform regular internal testing to check for new weaknesses, including password reuse. If an organization relies solely on external scanning, they risk missing out on identifying significant attack vectors that might exist within their network perimeter.
What Does Internal Network Penetration Testing Entail?
Sikich performs internal penetration testing in five phases. For the purposes of illustrating how Sikich approaches each of the phases during a penetration test, we will speak to each phase using a real-world engagement as an example. To maintain the client’s anonymity, we’ll refer to the organization as ACME CORP.
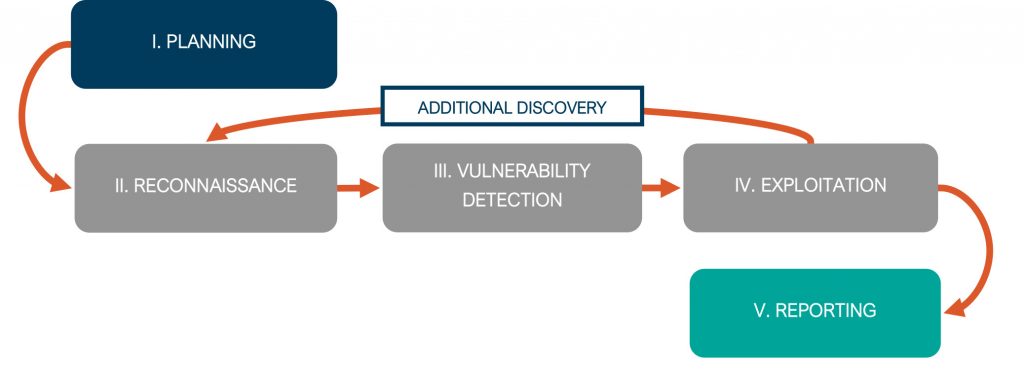
Phase I: Planning
During planning, Sikich works with the client to identify relevant targets and determine the client’s goals for the testing. ACME CORP. wanted to test the access from their “non-secure” environment into their “secure” environment, with the goal being to determine if the “secure” environment could be breached.
Phase II: Reconnaissance
In this phase, Sikich attempts to find and gather information about the targets identified during planning. For ACME CORP., Sikich performed scanning to detect hosts, servers, ports, printers, version information and more within the ACME CORP. environment. Sikich observed traffic on the network and found Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NetBIOS) protocols active in the “non-secure” environment. From the traffic, Sikich was able to capture password hashes for users, and later obtain the clear-text passwords through password cracking. After identifying a network path into the “secure” environment from the “non-secure” environment, Sikich used the credentials it had obtained earlier in the testing to gain access to that “secure” environment.
Phase III: Vulnerability Detection
As part of vulnerability detection, Sikich focuses on discovering vulnerabilities related to application security, access controls, network security, operating system security and user management. In the case of ACME CORP., Sikich found security misconfigurations in the internal firewall and identified that certain passwords had been reused.
Phase IV: Exploitation
Sikich takes the information discovered during vulnerability detection and uses it to take control of systems, impersonate users, obtain restricted access and perform tasks that demonstrate the potential consequences of such a compromise. Within the ACME CORP. system, Sikich was able to inject malware and then bypass all anti-malware programs on the network.
As part of the testing process, Sikich may repeat certain phases as we uncover more information.
Phase V: Reporting
Part of the value of a penetration test depends on the ability of the client to understand and take action on the results. Within our reports, Sikich aims to clearly define the scope of the testing, the methodology used and the results of the testing, and make recommendations to address any findings. Sikich presented ACME CORP. with its findings as well as steps ACME CORP. could take to enhance their security posture. ACME CORP. found the testing and reporting to be extremely beneficial and used the engagement as an opportunity to learn more about their environment and implement improvements in their security controls.
Avoiding the Trap
No one person, piece of hardware or software program is perfect. People use unsafe password practices. People misconfigure firewalls. Anti-virus anti-malware programs can be bypassed. That’s why it’s important to avoid blindly trusting the security controls that you think are in place. Put your security controls to the test at least once a year. Make sure the exercise goes beyond an automated vulnerability scan and includes manual testing performed by someone qualified and knowledgeable. If an attacker finds a way into your network, you want to make sure you’ve set yourself up to minimize the amount of damage they might be able to do. Should your organization require assistance performing penetration testing, reach out to Sikich’s team of cybersecurity experts, and they will be more than happy to help.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




