This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Three Free Ways to Help Protect Your Identity

In the end, it doesn’t matter how much time or money we place into our security systems; nothing ends up being 100% secure. The most common “weakest link” in every environment ends up being based on our identity. It is then no surprise that most of Microsoft’s security focus is around protecting identities.
When an attacker obtains your username/password (phishing is still the #1 method), they get to see all sorts of information that you have access to, and they spread out and get past all sorts of defenses. If you have been one of the unfortunate ones to experience an attacker getting your admin’s information, you know all too well the amount of havoc they can cause with that level of access is dangerous. In our efforts to protect our identities, we can look back a decade or more and see how we have evolved our password policies to be more rigorous (typically longer and more changes). Often our IT-based identity approach leads to sticky notes on monitors (or under keyboards) with our super secure passwords. There are all sorts of technologies available to get us away from passwords because of that weak link (ie. Biometrics, RSA, Windows Hello).
Moving into the cloud, Microsoft offers numerous options as part of the Office 365 service that can provide protections. I am listing a handful of the free options, because these are the easiest ones to start with before getting into some of the paid routes. The paid options usually come with E5+EMS or the new Microsoft 365 subscriptions.
Free
Portal branding
I recently came across an article that outlined a use case of modifying the login page. Sikich has been doing this for years with migrations, because we always felt it gave clients a sense of familiarity (and it just looks neat). I had never before put a security lens on this effort.
Consider this: you receive an email from Microsoft stating that you need to update your profile because of a security issue. You clicked on the link and you get to a page that looks exactly like the normal Office 365 login page. Since that looks normal to you, you go ahead and enter your information. Now the attacker has your information. On the flip side of that, during your migration we changed the graphic and added a company logo, you were used to see that when logging into your services. You get a message from Microsoft and clicked on the link, but wait, it doesn’t look like your normal page! (I’ll be the optimist here and assume that because the login page is different you would stop here and report this.)
This is the visual change (standard vs. modified):
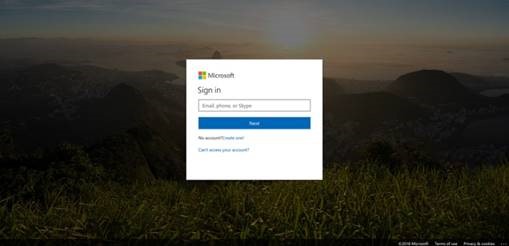
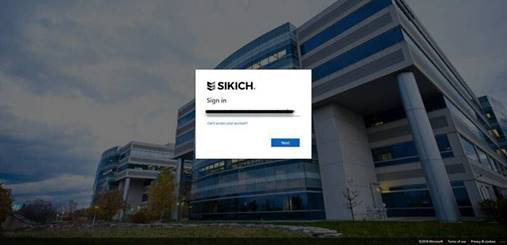 Multi-Factor Authentication
Multi-Factor Authentication
While there are some paid versions of MFA (adding all sorts of goodies), all the MFA deployments that I have completed over the years have all made use of the free version. It does exactly what I would want in terms of providing that second factor when logging into Office 365 (or anything setup with Azure SSO!). It is rather simple to deploy and troubleshoot, but it tends to take a fairly long time to get everyone through the enrollment process.
DKIM
Say what? DKIM stands for Domain-Keys Identified Mail. Still confused? I bet, as most people are. While this is not directly related to protecting your identity, I do believe that it has a role to play in that effort. DKIM is a method that proves any emails you send actually came from you (i.e. protection against spoofing). This provides indirect protection in that it can protect your customers/clients from possibly receiving spoof/phish emails that appear to be coming from you. Office 365 has a super simple way to get this enabled for your vanity domain. It’s free and offers some protection. How can you beat that?
Inexpensive
Advanced Threat Protection
The best $2/month you will ever spend on a security product for a user. See my past blog on ATP.
Contact Sikich to see about deploying these free Office 365 services to better protect your information and your identities.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




