A digital signature is a means of providing authenticity and integrity for application updates, messages, or other exchanges of data. The digital signing process relies on public-key infrastructure and the beauty of asymmetric encryption. This post will focus on how digital signatures work and what they can be used for. To learn more about how public and private key pairs are exchanged, please check out this previous blog post.
How Digital Signatures Work
Digital signatures consist of two main parts: the public/private key pair and a hash of the contents the sender needs signed. The first step is for the sender’s system to compute a hash of the data that needs to be signed. Second, the hash is encrypted with the sender’s private key. Next, the sender transmits the data and the signature to the recipient.
The recipient then obtains the sender’s public key so that the recipient can decrypt the hash. If the recipient can decrypt the hash with the sender’s public key, the recipient is assured that the message did, in fact, come for the sender (authenticity). Finally, the recipient calculates their own hash and compares it to the hash sent along with the original message. If the two hashes match, the recipient is assured that the contents had not been tampered with (integrity).
Application to Messages
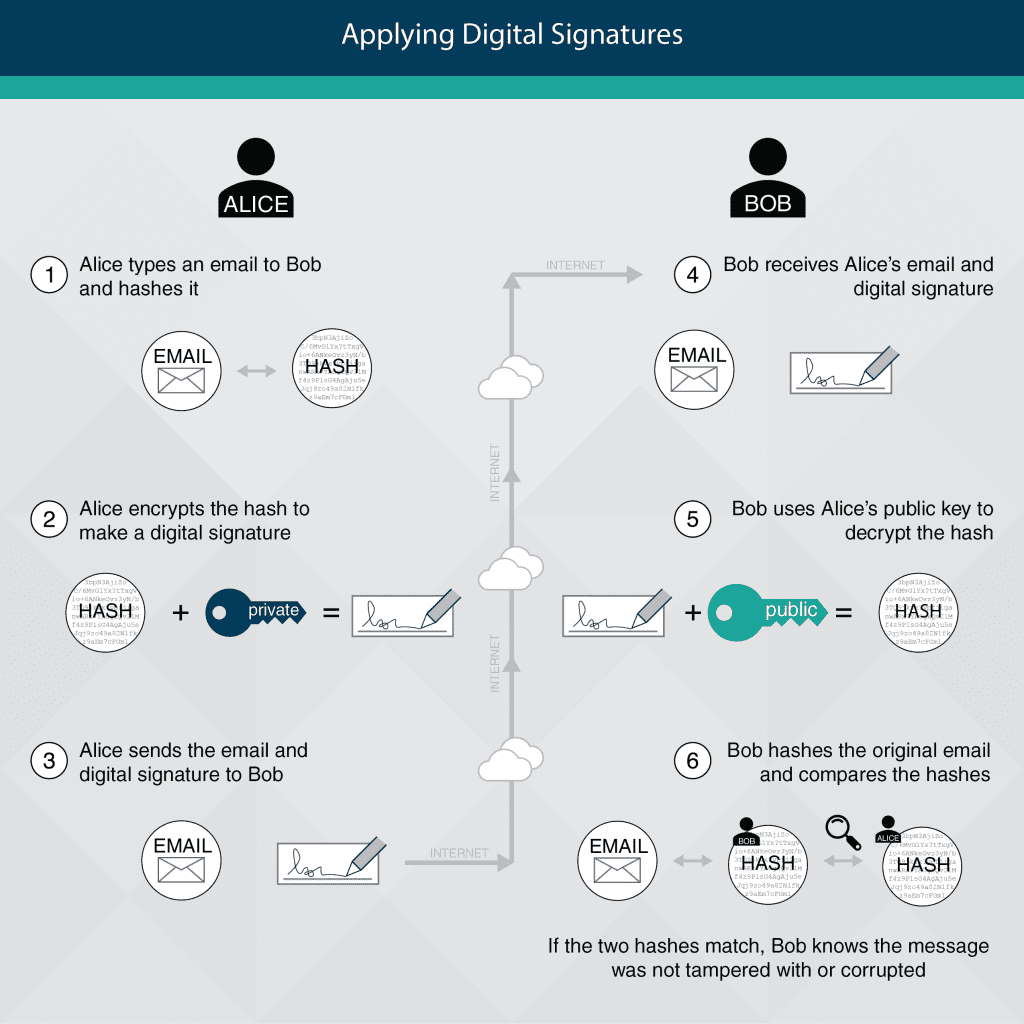
What does this have to do with me? To better understand how we can apply a digital signature to a message, let’s use a classic “Alice and Bob” example.
- Alice types an email to Bob.
- Alice’s computer calculates the hash of the email message and uses Alice’s private key to encrypt the hash.
- Alice sends the email to Bob, which includes the encrypted hash (the digital signature).
- Bob receives the email from Alice along with the digital signature.
- Bob uses Alice’s public key to decrypt the hash.
- Since Bob was successful in using Alice’s public key to decrypt the hash, Bob knows the message must have come from Alice.
- Bob’s computer calculates the hash of the original message.
- Bob’s computer then compares the two hashes to see if they match.
- If the two hashes mash, Bob knows that the message has not been tampered with or corrupted.
Code Signing
Can we use digital signatures to protect applications? Absolutely. While usually called code signing, the same principle applies to executables, libraries, firmware, and other sensitive application data. Before installing or running applications, code signing can demonstrate that the application came from the authorized source and that the data was not tampered with.
- Alice creates an application.
- Alice’s computer calculates the hash of the application and uses Alice’s private key to encrypt the hash.
- Bob downloads the application, which includes the encrypted hash (i.e., the digital signature).
- Bob uses Alice’s public key to decrypt the hash.
- Since Bob was successful in using Alice’s public key to decrypt the hash, Bob knows the application came from Alice.
- Bob’s computer calculates the hash of the application.
- Bob’s computer then compares the two hashes to see if they match.
- If the two hashes mash, Bob knows the application has not been tampered with or corrupted.
When it comes to code signing, a company’s key pairs are often authenticated by known, trusted third parties like Comodo, DigiCert, GlobalSign, and GoDaddy. The process behind this is a little more detailed, and we will discuss self-signed certificates versus certificates signed by a Certificate Authority (CA) in a future blog post.
If you have questions about digital signatures or want to discuss methods to enhance the security of your environment or data, reach out to our team at Sikich, and we’ll be happy to help.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.